What to Know
- Cybersecurity experts believe efforts are already underway to spread misinformation and undermine the credibility of the 2020 U.S. presidential election
- In the 2016 election season, intelligence suggests many high-profile data breaches were carried out by hackers in Russia. In 2020, there's evidence that much of the online meddling is coming from Iran
- Though there's concern over protecting vote-counting systems, experts say the greater threat is attempts to influence public opinion through social media and news manipulation
With Super Tuesday and the California primary election just days away, it went almost without saying that election hacking would be a hot topic at one of the world's biggest cybersecurity events.
"It's incredible if you think about how important the election process is to our American democracy — and the low level of security that's in place today," said Arctic Wolf senior vice president Dan Larson.
Reflecting on the high-profile hacks of the 2016 election cycle, Larson added, "That's one of the really frustrating things about election security. The breaches that we've seen occur, they're actually very preventable."
Larson, whose company offers a fully-staffed security operations center as a service to businesses and political campaigns, spoke to NBC Bay Area during the weeklong RSA Conference in San Francisco. The convention halls were crowded and bustling, even after several high-profile sponsors including IBM and Verizon canceled their appearances over coronavirus concerns.

Among the many exhibitors who remained, products to battle every conceivable kind of cyberattack were on display, including the pesky and dangerous threat known as "phishing."
Local
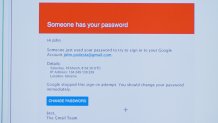
"What you're looking at is the actual message itself," explained Agari chief marketing officer Armen Najarian, as he scrolled through an official-looking security alert that appeared to come from Google's Gmail team.
Alas, the message wasn't from Google. But it was realistic enough to fool several campaign staffers working on Hillary Clinton's 2016 bid for the White House. Early on a Saturday morning, they scrambled to change a password they thought had been compromised, and in the process, handed Russian hackers the keys to campaign manager John Podesta's personal email account. Its contents, including sensitive and potentially embarrassing documents, were later leaked online.
Leaked documents and embarrassing personal information can be dramatically more damaging to a campaign if they're shared widely on social media — and cybercriminals don't need real human followers to do that.
"If you can look like a million humans, what can you do? And the answer is a lot of things," said Tamer Hassan, CEO and co-founder of White Ops.
White Ops studies and battles "botnets" — networks of a million or more tiny malware programs called "bots" that embed themselves on consumers' phones, laptops and tablets, and use their network connections to silently create and operate fake accounts on innumerable websites.
"What we have seen are influence operations that are targeting the electorate themselves," said FireEye head of global intelligence Sandra Joyce. "Trying to amplify (the attackers') ideas, trying to get people to vote a certain way."
Hassan added that the idea behind having a million bots retweet a fake news headline is actually not all that new.
"Computational influence has its roots in psychological warfare," he said. "It goes all the way back to the early '50s, the CIA operation in Guatemala, for example, where (the United States) took over one radio station and convinced an entire country of an invasion. That's a form of psychological influence."
Taking fake headlines a step further are "deepfakes:" realistic, fabricated recordings of candidates appearing to say something they never actually said.
"My team has even generated my own voice," said Pindrop CEO and co-founder Vijay Balasubramaniyan. "And they actually had my voice played for my wife, and she thought she was talking to me."
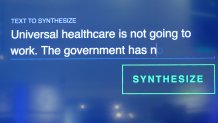
Pindrop has its roots in the call center arena, providing voice authentication technology for banks and insurance companies, among other large customers. But its next project will be a totally different animal: a browser plug-in that will let users know if the voice they're hearing appears to be synthesized.
"If you look carefully enough, you can detect artifacts of these machines generating them," Balasubramaniyan said, adding that in Pindrop's own research study, volunteers could only discern real from fake audio 57 percent of the time.
While those in cyber-intelligence say influence operations make up the bulk of the threats aimed at disrupting the 2020 election, there are still murmurs of hacking attempts on the voting process itself.
Companies like DUST Identity are focused on the complex problem of authenticating and tracking the hardware used to record and count votes, ensuring it's not compromised at the factory or tampered with at a polling place.

"We just want to make sure that when you're holding a device in your hand, you can trust it," said DUST Identity CEO and co-founder Ophir Gaathon.
DUST is an acronym that stands for "diamond unclonable security tag" — and that tag is, in fact, made of dust: microscopic diamond particles that bend light in very specific ways.
"We're spray coating the object with the diamond dust, and we allow Mother Nature to create a random pattern that we use to create that fingerprint," Gaathon said, and that diamond fingerprint is recorded in a database.
Circuit boards, hard drives, memory cards and tamper-evident tape can all be sprayed with the dust, so that election officials can tell if a machine has been opened, or if a critical part is out of place.
Of course, that means the one thing left for election officials to authenticate is the voters themselves. In many places, that's still done with paper logbooks at polling places, and state-issued driver's licenses or ID cards. But in Colorado, there's a more modern approach in the works.

"We've worked with the Colorado state government to create the first digital driver's license," said Richard Bird, chief customer information officer at Ping Identity.
Although Colorado state laws have yet to catch up with the technology, it could one day be a legally-accepted substitute for a physical driver's license. And unlike the cards that can be lost, stolen, faked or altered, Bird said the digital ones are verified online for authenticity each time they're presented.
"The real benefit," he said, "will be the ability for you to be able to vote anywhere. No longer do you walk into your polling place and be told, 'Oh, you had an old address and you're in the wrong polling place.' You'll be empowered to be able to vote in that election simply because you're able to confirm you are who you say you are."



